The Massive X Cyberattack has plunged the popular social media platform into chaos, leaving thousands of users across the globe unable to connect. On Monday, the notorious hacker group Dark Storm executed a powerful DDoS attack, resulting in a significant outage that was reported by more than 40,000 frustrated users on Downdetector. Error messages flooded the screens of those attempting to access X, illustrating the widespread disruption caused by this cybersecurity breach. As the dust settles, discussions continue to dominate cybersecurity news, with experts analyzing the implications of such a prominent attack orchestrated by a group purportedly linked to Russian interests. The incident not only raises questions about vulnerability in digital security but also highlights the alarming capabilities of modern hacker group attacks.
In recent events, a significant cyber offensive dubbed the Massive X Cyberattack has ignited controversy and concern. This incident, marked by a debilitating DDoS assault on the X platform, has triggered a wave of discussion in cybersecurity circles, particularly regarding the rising power of hacker collectives like Dark Storm. As users faced connectivity disruptions, the ramifications of the attack were felt worldwide, with many turning to social media to voice their frustrations. This recent surge of online volatility not only underscores the vulnerabilities of digital infrastructures but also amplifies the urgency for robust cybersecurity measures. Amidst the noise of this platform outage, it is critical to examine both the motivations behind such assaults and their potential long-lasting impacts on the digital landscape.
Understanding the Massive X Cyberattack
The Massive X Cyberattack that occurred recently revealed the vulnerabilities of major social media platforms like X. This DDoS attack, orchestrated by the infamous hacker group Dark Storm, left thousands of users unable to access their accounts, signifying potential weaknesses in the cybersecurity frameworks that are supposed to protect users online. As awareness around data security heightens, incidents such as this remind companies of the urgent need to fortify their defenses against increasingly sophisticated cyber threats.
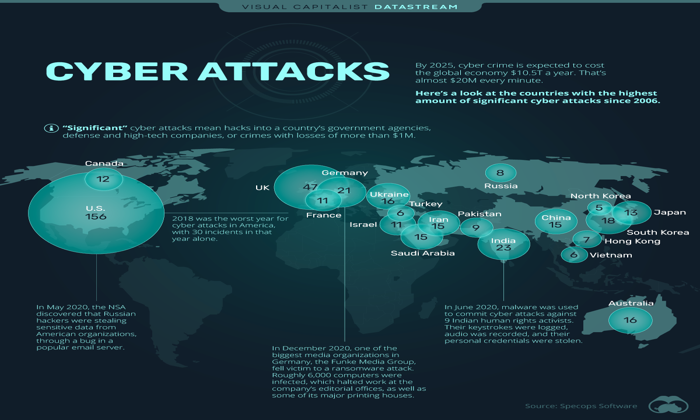
Victims of the attack faced considerable inconvenience, with reports showing a spike in complaints reaching up to 40,000 during the height of the outage. The incident certainly raised alarm bells within the cybersecurity community, as it highlighted the persistent threat posed by hacker groups like Dark Storm. Through aggressive tactics and boasting about their capabilities via channels like Telegram, they have managed to capture the attention of SOC teams worldwide, prompting urgent discussions on enhancing digital safety protocols.
The Role of Dark Storm in the Cyberattack
Dark Storm, a hacker group with alleged ties to Russia, has made waves in the cybersecurity news arena. This group is notorious for launching DDoS attacks, taking advantage of their technical skills to create disruption across large platforms. Their claimed responsibility for the Massive X Cyberattack is significant, as it raises questions about their motivations and possible political agendas, especially given their history of targeting NATO countries. While their spokesperson emphasized that the recent attack was a demonstration of capability rather than a politically charged mission, the implications remain troubling.
The connection of Dark Storm’s actions to the ongoing political turbulence in various countries cannot be overlooked. Their attacks coincided with rising tensions surrounding popular figures and governmental policies, particularly against the backdrop of protests against Elon Musk’s initiatives. As potential motivations are debated, it’s clear that hacker groups not only strive to showcase their technical prowess but may also engage in cyber warfare to influence public opinion and stir unrest.
Impacts of the DDoS Attack on X Users
The consequences of the Massive X Cyberattack ripple through the X user base, illustrating the fragility of online platforms under cyber threats. With functionality interrupted for extended periods, users experienced frustration and disbelief as they were met with error messages and connectivity issues. This incident has drawn critical awareness to the necessity for advanced DDoS mitigation strategies, as well as proactive communication from platforms during such outages to keep users informed.
Moreover, the attack has sparked conversations regarding data privacy and platform reliability. As thousands scrambled to regain access, some questioned the adequacy of X’s cybersecurity measures. Enhanced communication protocols, transparent updates during crises, and improved threat detection systems are essential takeaways for social media companies to ensure user trust and operational continuity during attacks that could arise from hacker groups like Dark Storm.
Insights from Cybersecurity Experts on Mitigating Threats
In the aftermath of the Massive X Cyberattack, cybersecurity experts emphasize the urgency of reviewing and updating security protocols across social media platforms. The complexities of DDoS attacks require sophisticated preventive measures, which include behavioral analytics and improved traffic filtering that can effectively mitigate such threats. Security firms like SpyoSecure have been at the forefront of addressing these issues, offering actionable insights to organizations facing the possibility of similar attacks.
Moreover, education on cybersecurity practices remains paramount. Users often become the weakest link; hence, platforms should invest in awareness campaigns that foster secure online behaviors. As Dark Storm and similar hacker groups continue to evolve their tactics, a comprehensive approach to cybersecurity encompassing technology, education, and community vigilance is necessary to safeguard users against future cyberattacks.
How the X Platform Outage Affects Business Operations
The Massive X Cyberattack not only disrupted user access but also posed significant challenges for businesses relying on the platform as part of their marketing and communication strategies. The interruption of service could lead to lost revenue opportunities, as companies that utilize X to connect with customers were rendered temporarily invisible. The aftermath of such attacks encourages businesses to diversify their channels and not become overly reliant on a single platform.
In the wake of the outage, businesses are urged to revisit their crisis communication plans, ensuring they have protocols in place for any unforeseen downtime. This highlights the importance of strategic contingency planning in the digital age, where operations can be directly impacted by external cyber threats. Resilience in business practices requires not only technological investments but also a commitment to effectively communicating with stakeholders during disruptive events.
Community Reactions and Implications
The community response following the Massive X Cyberattack was immediate and loud, echoing the collective frustration experienced by individuals impacted by the outage. Many users took to alternative platforms to express their outrage, discuss theories about Dark Storm, and share personal experiences during the attack. This dynamic illustrates the role of social media as a vital communication tool, especially in times of distress when conventional platforms fail.
In addition, the fallout from the attack underscores the collaborative effort required from both users and platforms in addressing cybersecurity challenges. Discussions among online communities have increased awareness of cyber threats while encouraging users to adopt better security practices. As public interest in cybersecurity heightens, this underlines a critical shift towards a more informed and prepared online user base capable of navigating risks associated with emerging digital threats.
Looking Ahead: Future Cybersecurity Measures
As organizations reflect on the lessons learned from the Massive X Cyberattack, the implementation of future cybersecurity measures becomes all the more pressing. Experts recommend a layered security approach that includes continuous monitoring for anomalies and a swift incident response framework. By adopting these proactive measures, companies can build resilience against future DDoS attacks and other cybersecurity threats posed by groups like Dark Storm.
Furthermore, engaging in partnerships with cybersecurity firms could provide organizations with access to the latest technologies and threat intelligence. By pooling resources and expertise, a more fortified virtual environment can be established that not only protects businesses but also secures user data against potential breaches. Strengthening the foundations of online safety is crucial as threats evolve and an ever-changing digital landscape continues to unfold.
Government and Regulatory Response to Cyber Threats
The Massive X Cyberattack has reignited discussions among policymakers about the necessity of stringent regulations to combat the rising tide of cyber threats. With groups like Dark Storm demonstrating their ability to compromise critical systems, governments are urged to collaborate on a global scale to establish unified cybersecurity frameworks. This could involve creating standards that not only protect individual platforms but also safeguard the interests of users across borders.
In response, regulatory bodies are beginning to explore the introduction of cyber hygiene standards that companies must adhere to. These regulations would serve as a benchmark for organizational preparedness against cyberattacks while promoting a culture of accountability within the tech industry. The hope is that a cohesive effort among governments, businesses, and cybersecurity experts will foster a safer digital environment for all.
The Future of Cybersecurity in Social Media Platforms
As the dust settles following the Massive X Cyberattack, the future of cybersecurity in social media platforms is under scrutiny. Platforms must prioritize the enhancement of their security infrastructures, adopting innovative technologies such as machine learning and AI to identify and combat cyber threats in real-time. The rapidly evolving threat landscape necessitates a shift in focus toward anticipating hacker group attacks rather than merely responding to them.
Moreover, the integration of user feedback in the development of cybersecurity strategies is critical. Users who actively report vulnerabilities and potential risks can significantly bolster a platform’s defense mechanisms. By tapping into the collective insights of the user community, social media platforms can create a more robust security apparatus, reinforcing trust and ensuring a safer environment for their users.
Frequently Asked Questions
What is the Massive X Cyberattack and who is behind it?
The Massive X Cyberattack refers to a DDoS attack executed by a hacker group named Dark Storm, which has been linked to Russia. This cyberattack led to a widespread outage of the X platform, disrupting access for thousands of users worldwide.
How did the Dark Storm hackers conduct the Massive X Cyberattack?
The Dark Storm hackers conducted the Massive X Cyberattack through a distributed denial-of-service (DDoS) assault, overwhelming the platform’s servers and causing connectivity issues for users, as reported by cybersecurity experts.
What were the effects of the Massive X Cyberattack on the X platform?
The Massive X Cyberattack resulted in significant service disruptions for users, with error messages and connectivity failures reported by over 40,000 individuals at its peak. The platform experienced instability for several hours before service was restored.
How did Elon Musk respond to the Massive X Cyberattack?
Elon Musk confirmed the occurrence of the Massive X Cyberattack during an interview and revealed that his team traced the hackers’ IP addresses to the Ukraine region, providing insight into the potential origin of the DDoS attack.
What are the motives behind the Dark Storm hacker group’s attack on X?
While Dark Storm’s attack on X is claimed to be a show of force, their history of targeting NATO countries and their pro-Palestinian stance indicates deeper political motivations behind the Massive X Cyberattack.
What can users do about the impacts of the Massive X Cyberattack?
Users experiencing outages from the Massive X Cyberattack should stay updated through cybersecurity news outlets and the X platform’s official channels for recovery information, while practicing good cybersecurity hygiene to protect their accounts.
Is the X platform safe after the Massive X Cyberattack?
Following the Massive X Cyberattack, the X platform has worked to restore functionality. However, users are advised to remain vigilant and follow cybersecurity best practices to ensure their safety online.
What cybersecurity measures are being taken after the Massive X Cyberattack?
In response to the Massive X Cyberattack, cybersecurity firms and the X platform’s team are likely analyzing the attack vectors and reinforcing their security protocols to better protect against future DDoS attacks.
How does the massive X Cyberattack relate to ongoing political tensions?
The Massive X Cyberattack highlights the intersection of cybersecurity and politics, especially given the hacker group’s connections to ongoing protests against Elon Musk and his policies, which may reflect a broader narrative of political dissent.
| Key Points | Details |
|---|---|
| DDoS Attack on Platform X | The hacker group Dark Storm launched a Distributed Denial-of-Service (DDoS) attack affecting thousands of users globally. |
| Peak Complaints | Downdetector recorded a peak of 40,000 user complaints during the attack. |
| Hackers’ Alleged Identity | Dark Storm has alleged ties to Russia and claimed responsibility for the attack. |
| IP Tracing | IP addresses traced back to the Ukraine region as per Elon Musk’s team. |
| Telegram Communication | The leader of Dark Storm announced the attack via a now-deleted Telegram post. |
| Motives Behind the Attack | While the group claims political disinterest, its history of targeting NATO countries and a pro-Palestinian stance contradicts this. |
| Political Context | The attack coincides with protests against Elon Musk’s initiatives, particularly the ‘Take Down Tesla’ movement. |
Summary
The Massive X Cyberattack has raised alarms internationally as the hacker group Dark Storm claimed responsibility for launching a severe DDoS attack that disrupted access to the platform for thousands. Amidst increasing connectivity issues reported globally, questions surrounding the motivations and affiliations of the attackers have surfaced, especially given their alleged ties to Russia and a history of targeting NATO countries. The attack not only highlights vulnerabilities in digital infrastructure but also unfolds against a backdrop of political tensions involving Elon Musk, further complicating the narrative of this significant cyber incident.
The recent Massive X Cyberattack has sent shockwaves through social media users worldwide, leaving thousands unable to access the platform amidst connectivity failures. Launched by the notorious hacker group Dark Storm, this DDoS attack unfolded with alarming speed, resulting in a significant X platform outage that drew attention from cybersecurity news outlets globally. Reports indicated that over 40,000 complaints were logged in just a few hours, highlighting the magnitude of the disruption. As the chaos unfolded, Dark Storm’s leader took to a now-deleted Telegram channel to boast about their successful strike against the platform, raising concerns about the motivations behind such serious cyberattacks. This incident is not just a tech issue; it’s a vivid reminder of the ongoing cybersecurity threats that challenge our digital landscape daily.
In what can be described as a significant breach of digital security, a massive cyber onslaught has crippled the widely-used X platform, rendering it inaccessible for numerous users. This incident, attributed to an aggressive hacker faction known as Dark Storm, is a classic example of a distributed denial-of-service (DDoS) attack—a tactic that overwhelms platforms and disrupts online services. The implications of this high-profile cybersecurity event ripple throughout the tech community and raise urgent questions about protective measures against similar aggressions. As discussions intensify within cybersecurity circles, the role of hacker collectives and their influence on social infrastructures comes under scrutiny, further emphasizing the critical nature of enhancing our defenses against future breaches.